Cyber conflict is no longer a niche concern for defense departments, it’s a pervasive, persistent threat reshaping the security posture of every enterprise. As global tensions escalate—from Ukraine and Israel to rising flashpoints in South Asia—cyberwarfare has emerged as the new frontline. It targets not just military infrastructure, but also cloud platforms, supply chains, tech ecosystems, social media feeds, and the smartphones of your employees.
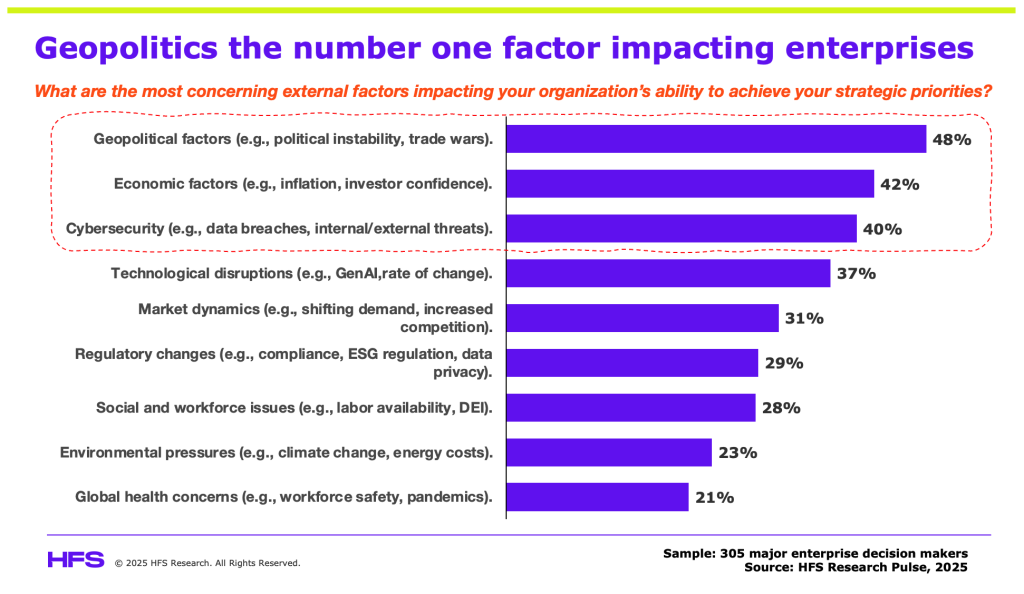
It is little wonder our latest research shows the combo of geopolitics, economics, and cybersecurity as the dominant external factors on the minds of G2K enterprise leaders:
This is not just about ransomware or phishing; it’s an emphatic focus for the CIO
Cyber conflict today includes information warfare, infrastructure sabotage, and financial system disruption, all designed to paralyze confidence and destabilize economies.
The pressure point has become the CIO, who not only has to manage significant pressures from their boards and leadership peers to deliver an AI agenda, but they also have to balance this with a proactive, holistic cybersecurity approach that business leaders can comprehend. Mess up your cybersecurity, and you’re not only fired, but your entire firm may just sink with you. And for every cyber-attack that goes public, we estimate another six are kept under wraps to avoid negative publicity, remaining unreported or even undetected:
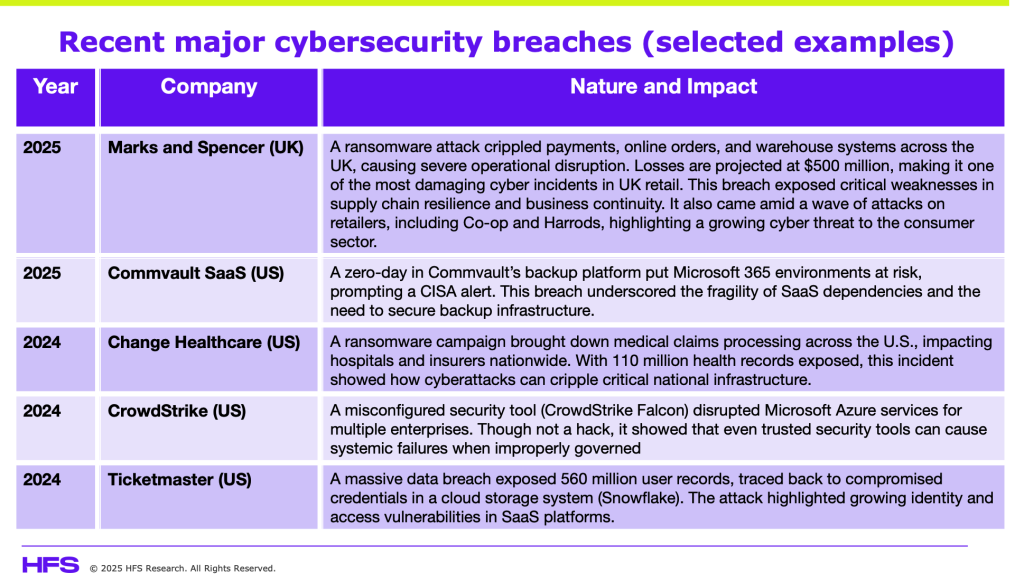
Enterprise leaders must treat cybersecurity as a strategic boardroom issue, not merely an IT function
This is why we do not believe a CISO should report to the CEO, as the CEO really needs to understand the risks and how to proactively get ahead of them. CISOs tend to be too technical, whereas the CIO is evolving as the hybrid executive who can translate technical issues in plain business terms. In addition, with all the pressure to deliver on AI, the CIO is best placed to bring the cyber strategy into the conversation, as there simply won’t be successful AI without an effective cyber strategy.
This paper unpacks the modern cyberwarfare playbook, outlines its enterprise implications, and provides a security readiness agenda that organizations must prioritize in an era of digital warfare.
Cyber tactics are now strategic weapons of war
Before diving into each tactic in depth, the table below summarizes the most common cyberwarfare methods, their typical targets, intended impacts, and real-world examples observed in recent conflicts.
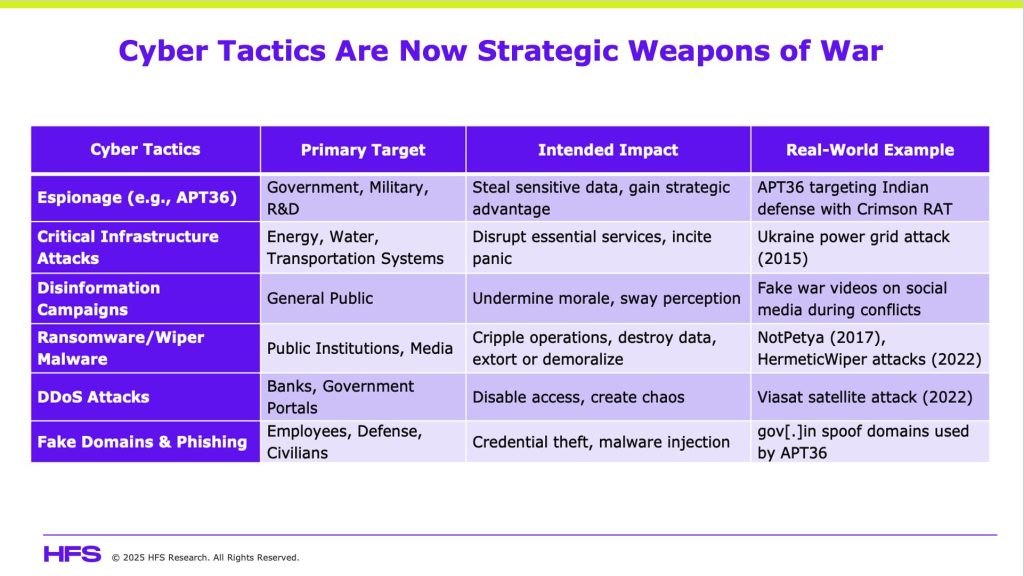
Let’s now examine these threats in greater detail:
- Cyber Espionage Is a Silent Strategic Weapon
Cyber espionage is among the most insidious tactics in modern cyberwarfare. It involves stealthy infiltration into government networks, defense systems, and critical infrastructure to extract sensitive information—military strategies, diplomatic communications, or classified research. These campaigns are often the work of state-sponsored Advanced Persistent Threats (APTs). The long dwell times and covert nature of these breaches make them especially dangerous, and they can unfold undetected for months, quietly eroding national security.
- Sabotage of Critical Infrastructure
Attacks on critical infrastructure are no longer speculative, they are documented weapons of war. Power grids, water supply systems, transportation hubs, telecom, and financial institutions are prime targets due to their symbolic and systemic value. Disabling such services can incite public panic, disrupt military logistics, and hobble a nation’s economy.
- Denial-of-Service (DoS/DDoS) Attacks
Distributed Denial-of-Service (DDoS) attacks involve flooding a target’s servers or websites with overwhelming traffic, making them inaccessible. These attacks often aim to paralyze essential services like banking, government portals, or emergency response systems during times of peak demand. In recent conflicts, banks have established “war rooms” to monitor and neutralize such attacks on financial infrastructure, recognizing that even temporary outages can cause economic damage.
- Disinformation and Psychological Warfare
Modern cyberwarfare also weaponizes information. State-sponsored troll farms, fake social media profiles, and AI-generated content flood platforms with misinformation designed to erode public trust or manipulate opinion. During active conflicts, fake videos, doctored images, and viral rumours often circulate faster than facts. The goal is not just confusion—it’s psychological destabilization.
- Ransomware and Wiper Malware
Ransomware typically locks critical files and demands payment for their release, while wiper malware is designed purely to destroy data. In war zones, these tools can disrupt media outlets, hospitals, transportation, and public sector databases.
- Fake Domain Attacks and Social Engineering
Threat actors often register lookalike domains, like “gov[.]in” clones or fake military emails to deceive targets. These are used in phishing attacks to steal credentials or implant malware. These tactics, as seen with actors like APT36, exploit human trust as much as technology. This reinforces that cyberwarfare doesn’t always involve zero-days or advanced code—human deception remains one of the most effective vectors.
Cyber risk now reaches every node—from the boardroom to the smartphone
The broad reach of cyberwarfare means that no one is immune—not just governments and militaries, but also hospitals, utilities, media, private enterprises, and ordinary citizens.
Governments and National Security
Defense ministries, intelligence agencies, and critical infrastructure operators are prime targets. The need for robust cyber defense postures, including threat intelligence sharing, rapid incident response, and sovereign cloud strategies, has never been more urgent. Enterprises must integrate with national threat intelligence initiatives and not operate in silos—public-private cyber cooperation is now survival, not strategy.
Financial Institutions and Corporations
Banks, payment processors, and fintech firms are increasingly in the crosshairs of both nation-state actors and criminal proxies. Disruption of financial services not only causes direct economic loss but also undermines national morale and investor confidence. CISOs and CFOs must jointly model the impact of multi-day outages—not just from a tech standpoint, but investor confidence and liquidity.
Citizens and Civil Society
Ordinary users are not exempt. Malware-laced videos, phishing messages on messaging apps, and spyware hidden in mobile content put smartphones and personal data at risk. These devices can also be hijacked into botnets or used as entry points into corporate systems.
Security can no longer be just a defense—it must be a digital war doctrine
The shifting cyber risk landscape demands more than patchwork defenses—it requires holistic, governance-driven frameworks across all levels of society.
For Individuals:
Individuals are no longer bystanders in digital conflict. Practicing basic cyber hygiene—strong passwords, MFA, regular updates, and healthy skepticism on social media—must become habitual. Each personal device is part of a nation’s cyber terrain.
For Organizations:
- Operationalize war-room readiness: Crisis simulations and red-teaming must become part of quarterly risk oversight.
- Elevate employee awareness: Training must go beyond phishing modules—employees must understand geopolitical vectors and supply chain infiltration.
- Audit digital supply chains continuously: Most vulnerabilities now enter through cloud vendors and third-party platforms.
- Backups are not optional: They must be segregated, immutable, and tested frequently.
For Boardrooms and Policy Leaders:
Leadership must stop asking if cyberwar will affect them—and start preparing for when it does. Key questions every board must ask today:
- Do we have strategic visibility into our cloud, SaaS, and geopolitical risk exposure?
- Can we maintain operations during a symbolic, high-profile cyberattack?
- How will we defend brand trust if misinformation targeting our leadership goes viral?
Global cyber instability demands enterprise engagement in rulemaking
In the absence of attribution standards, the private sector is often left to interpret silence as safety. Enterprises must advocate for clearer norms and participate in attribution consortia and not wait for government-led rules to trickle down. Enterprises cannot wait for digital Geneva Conventions. Industry coalitions must take the lead in defining cyber accountability protocols, especially in cross-border supply chains and critical services.
These costs are cascading to enterprises through compliance mandates, insurance premiums, and operational disruptions. Leadership must start quantifying cyber conflict readiness as a financial exposure in annual reports and audits.
Bottom Line: Cyber conflict is now a business continuity threat, a brand risk, and a geopolitical wildcard.
Cyber conflict is now a business continuity threat, a brand risk, and a geopolitical wildcard. Enterprise leaders must treat it with the same urgency and discipline as they do financial risk or regulatory exposure. It’s time to move beyond firewalls and frameworks to establish a living cyber doctrine—one that includes red-teaming, board-level risk modeling, threat-sharing participation, and scenario-based preparedness.
The question is no longer if you’ll be targeted. It’s whether you’re prepared to respond at the speed of a nation-state actor.
Act now: appoint a cyber conflict readiness officer, fund cyber resilience as an innovation stream, and demand geopolitical threat briefings at the board level. Because resilience in the age of cyberwar isn’t just technical—it’s cultural, strategic, and existential.
Posted in : Cybersecurity, Politics